Detect third party data breaches
Cybercriminals are constantly trying to access your data. Monitoring of external data breaches protects and warns employees when their information is exposed in a data breach by a third party.
Cybercriminals are constantly trying to access your data. Monitoring of external data breaches protects and warns employees when their information is exposed in a data breach by a third party.

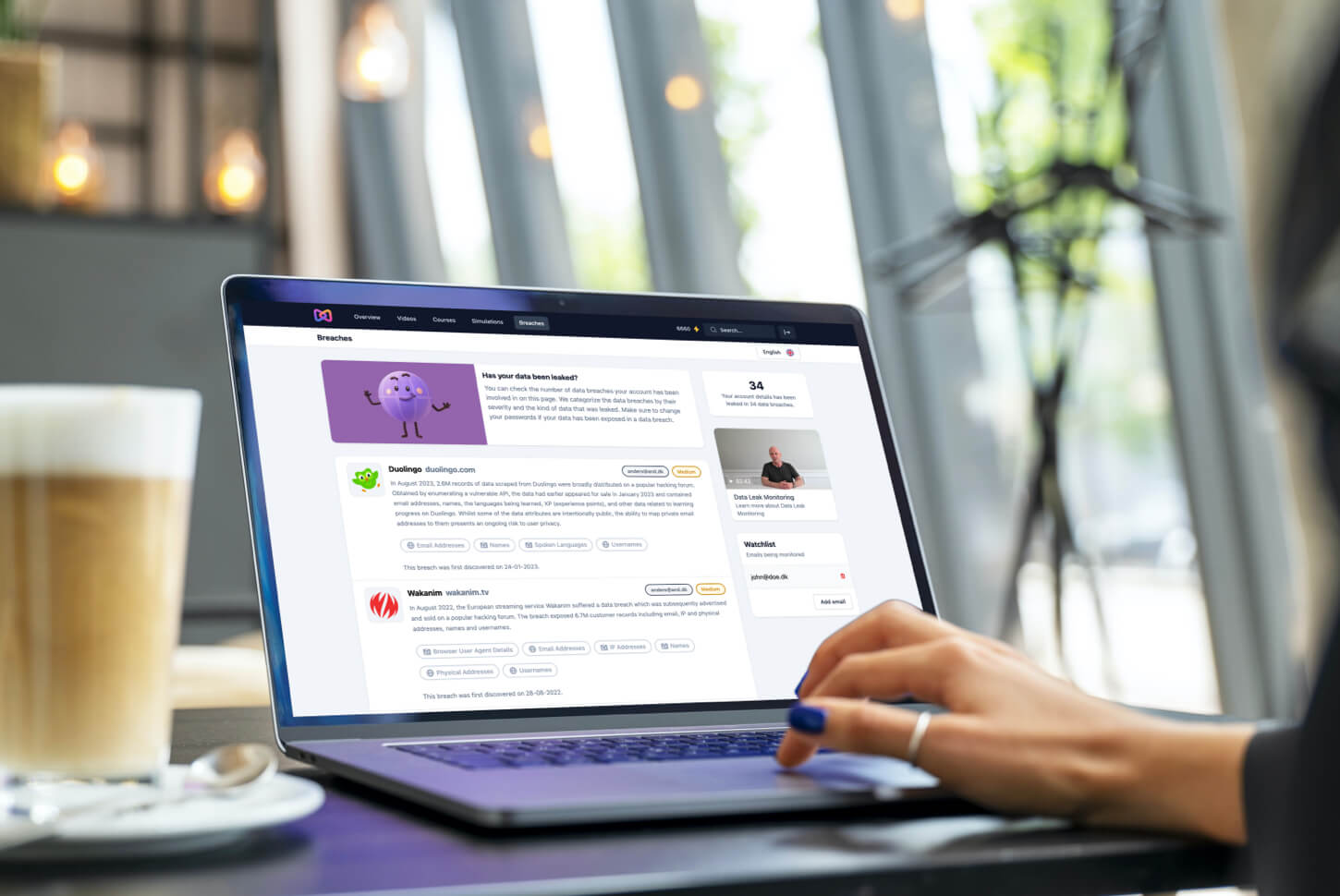
The employees always have access to an overview of the data breaches in which their information has been exposed. If a new data breach leaks their information, they will be notified immediately.
We compare the employees' information with hundreds of millions of data points, which are continuously collected from external data breaches. Employees automatically receive an alert if their information is leaked in a new data breach.
By notifying the employees, they have the opportunity to prevent compromise of their accounts. It protects both the employees and the company.

Employees can opt for monitoring leaks of their private data. It helps prevent compromise of the employees’ private accounts while protecting the company if the employees reuse their passwords.
The monitoring of private data is completely optional and adds an extra layer of security - both for the employees and for the company.
We categorize data breaches according to the severity of the exposed information. If a data breach exposes information with a high degree of severity, we categorize the data breach as critical.
The employees can instantly see if a data breach is critical, so they can prioritize which information needs to be changed first.

Discover how Moxso's features can assist you.
During onboarding, the data breach monitoring is set up automatically for all employees.
Data categorization
The employees can see what kind of information that has been leaked in a data breach.
Updated database
We maintain a continuously updated database of leaked data with hundreds of millions of data points.
Good cyber hygiene
When the employees change passwords after a data breach, they increase the overall cybersecurity of the company.
Increased security
The monitoring reduces the risk that cybercriminals exploit employees' exposed data to gain access to the company.
Increased attention
The employees naturally become more aware of the use of passwords and their importance.
Instant overview
The employees get an overview of all historical data breaches that have exposed their information.

“The switch to gamification and positive learning has been a game changer for us. Moxso’s easy-to-understand examples of real-world threats and insights into every single employee’s progression, has made me confident that Moxso’s training program is the best solution for Fireball.”
Liselotte Lund-Rasmussen
Partner - Fireball

Data leak monitoring is a tool that employees can actively use to prevent data leaks from turning into hacker attacks.
In this white paper you will learn:
The risks of data leaks and how often they happen
How to use monitoring to mitigate specific risks
Everything you need to know
The cybersecurity experts at Moxso in charge of the data breach monitoring start by setting up a notification channel to a data provider. Then they choose what kind of data we want to collect. The data we collect is personal information, including password, e-mail address, username, API tokens, address, spoken languages and more.
Our data providers are continuously searching the web for data breaches containing the kinds of data we want to collect. They search for data breaches and data leaks on the surface web, the deep web, and the dark web. When data breaches happen and the data providers identify the leaked data, we receive a notification and are able to collect that data for our database immediately.
We continuously compare data from your employees with the data collected from external data breaches. If there is a match, which means that your employees' data has been compromised in an external data breach, we send an alert to the employee or employees so that they can act as fast as possible and protect their compromised data and your company.
A general data breach occurs if information is stolen or taken without the knowledge or permission of the owner of the information. All companies, both big and small businesses, can fall victim to a data breach.
Stolen data can involve sensitive, personal, or confidential information such as credit card numbers, phone numbers, driver's license numbers, social security numbers, customer information, employee data, trade secrets, and protected information.
More specifically, data breaches can also be seen as a breach of personal data. A breach of personal data occurs if, according to the Danish Data Protection Agency, it "leads to accidental or illegal destruction, loss, alteration, unauthorized disclosure of or access to personally identifiable information that has been transmitted, stored or otherwise processed".
Personal data security breaches can happen if a company's data controller's IT systems with personal data are not sufficiently well protected, allowing third parties to gain unauthorized access to the information. This can happen if the IT systems get hacked.
The most common hacks are social engineering attacks, such as phishing attacks, and malware attacks.
A breach of personal data security can also happen if the data controller does not take the necessary precautions and either intentionally or unintentionally passes on or changes personal details in the personally identifiable information.
If there is a breach of personal data and the personal data ends up in the wrong hands, the company risks having to notify both the Danish Data Protection Agency and the people who have had their personal information exposed. If the breach of personal data likely leads to consequences for the persons involved, the company must notify the affected individuals.
Due to the rules in GDPR, which came into effect in 2018, there is a general obligation for all data controllers to report breaches of personal data to the Danish Data Protection Agency. The actual report must be made without undue delay and no later than 72 hours after the data controller has become aware of the incident.
Possible damaging effects of a data breach can be damage to the company's reputation due to a perceived "breach of trust". Often, companies issue a public announcement that can lead to mistrust or loss of customers. The company and their customers may also suffer financial losses if the data breach leads to data loss or theft of money.
Due to the stolen information, data breach victims can fall victim to identity theft, payment card fraud, damaging attacks and more.
If a data controller is unable to report the breach, the Danish Data Protection Agency can submit a report to the appropriate authorities, which can result in a fine for the company.
This is why it's crucial to be aware of leaked information and potential data breaches.
A data leak occurs when sensitive data is accidentally exposed physically, on the Internet or in any other way. This can happen due to incorrect processing of personal data, for example when an employee sends an e-mail with personal information to an incorrect recipient. A data leak can also happen if an employee loses physical hardware, for example forgets a USB with confidential information on the train.
If a data leak occurs through physical exposure or exposure on the web, cybercriminals can relatively easily get access to that data, which can lead to cyberattacks like ransomware attacks.
While the terms (general) data breaches and data leaks are often used interchangeably, they are two separate data exposure types:
If a cybercriminal detects a data leak, the exposed data can be used to plan a successful cyberattack. So, by detecting and remedying data leaks before they are detected, the risk of data breaches is significantly reduced.
For the monitoring of data breaches, we use data from "Have i been pwnd?" and "Dehashed". Both data providers maintain a comprehensive database of leaked data from most data breaches online. By collecting data from the two data providers, we can update our database every day. The database contains several million data points from external data breaches.
If your employees' personal information is leaked in an external data breach, we will notify them immediately. Subsequently, employees must deal with the breach by changing the password, or other types of information, to the account from which the information has been leaked.
If employees use the same password for other accounts, they must also change the password for those accounts.
By changing the passwords for the affected accounts, your employees can most likely prevent hackers from accessing the accounts and exploit the associated data.
One of the most important security measures in cybersecurity is using strong passwords and changing your passwords regularly.
By updating your employees on leaks of their personal information, they naturally become more aware of what passwords they use and whether they reuse passwords. A lot of people reuse passwords or make variations of the same password or a commonly used password.
However, it's an example of poor cybersecurity hygiene as hackers use leaked passwords and variations of them to try to log onto many different accounts. Therefore, a hacker can gain access to many accounts with sensitive and confidential personal information if they just get hold of one password.
By changing the password for the accounts that have been compromised, the general cybersecurity of the employees in the company increases. If employees opt to get notified on leaks of their private data, their personal security also increases.
Whenever your employees set up new accounts, they will also be aware of the passwords and usernames, that they shouldn't use again.
Your employees can access their personal e-learning hub at any time. They can find an overview over leaked data under the section "Data breaches".
When clicking on the section "Data breaches", your employees will be presented with the data breaches that has exposed their personal information (if there are any). They can read about the data breach and see what kinds of information that has been exposed.
Moxso categorizes the data breaches and the individual information types after their severity, so your employees can prioritize the most serious data breaches first.
Cybercriminals responsible for data breaches usually start by targeting companies, rather than specific individuals. They want to get their hands on stolen credentials from as many people as possible so they can exploit, resell, or leverage it to make money.
Cybercriminals' target all kinds of personal information and credentials. That’s why cybercriminals often target huge companies with millions of users. These hackers look for common vulnerabilities and the hackers learn quite quickly how to exploit them. They only need to crack one password to an account to get access to a company's data or systems.
All types of data can be valuable to a hacker. Some data like banking information, bank card numbers, government-issued ID numbers, and PIN numbers is valuable because it can be used to steal the victim’s identity or withdraw money.
Through identity theft, cybercriminals can open new credit cards or apply for loans in the victims' names. By getting access to others' financial information, they can make big purchases or withdrawals. These hackers can even find ways to target their victims' friends and family once they gain access to their victims' e-mail and in doing so stealing sensitive data from a lot of people close to the victim.
E-mail addresses and passwords are also valuable because hackers can try to log onto many accounts using them. Hackers know that many people reuse the same passwords.